Om Token: A Comprehensive Guide
Understanding the concept of a token can be quite intricate, especially when it comes to its various applications and uses. In this article, we will delve into the world of Om Tokens, exploring their significance, functionalities, and how they are utilized across different platforms and industries.
What is an Om Token?
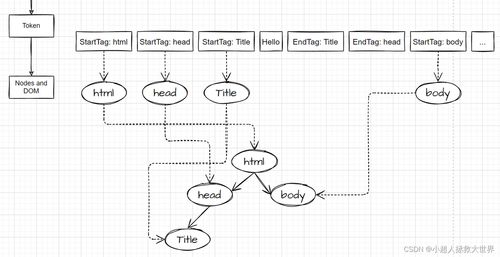
An Om Token, often referred to as a “token,” is a unique string of characters generated by a server to serve as an identifier for a client. It is commonly used in web applications and services to authenticate and authorize users, ensuring secure access to protected resources and functionalities.
Let’s take a closer look at the key aspects of an Om Token:
| Aspect | Description |
|---|---|
| Authentication | An Om Token is used to verify the identity of a user, allowing them to access restricted areas of a website or application. |
| Authorization | Once authenticated, the Om Token grants specific permissions to the user, determining what actions they can perform within the system. |
| Statelessness | Om Tokens enable stateless authentication, meaning that the server does not need to store any session information, reducing the risk of data breaches and improving scalability. |
Now that we have a basic understanding of what an Om Token is, let’s explore its applications in different scenarios.
Applications of Om Tokens
Om Tokens are widely used in various industries and platforms. Here are some common applications:
Web Applications
In web applications, Om Tokens are primarily used for user authentication and authorization. They provide a secure way to manage user sessions and ensure that only authorized users can access sensitive information or perform critical actions.
APIs
Om Tokens are extensively used in APIs to authenticate and authorize requests made by clients. They enable secure communication between different services and ensure that only legitimate requests are processed.
Mobile Applications
Mobile applications often utilize Om Tokens to authenticate users and provide access to specific features or functionalities. They help in maintaining a seamless user experience by eliminating the need for repeated login credentials.
IoT Devices
Om Tokens are also used in IoT devices to authenticate and authorize access to device functionalities. They ensure that only authorized users or systems can interact with the devices, enhancing security and preventing unauthorized access.
Types of Om Tokens
There are several types of Om Tokens, each serving different purposes. Here are some commonly used types:
- JSON Web Tokens (JWT): JWTs are self-contained tokens that encode claims about a user, such as their identity, roles, and permissions. They are widely used for authentication and authorization in web applications.
- OAuth Tokens: OAuth Tokens are used for authorization purposes, allowing third-party applications to access protected resources on behalf of a user.
- Bearer Tokens: Bearer Tokens are a type of access token used for authentication and authorization in APIs. They are typically included in the HTTP Authorization header.
Understanding the different types of Om Tokens is crucial in selecting the appropriate one for a specific use case.
Security Considerations
While Om Tokens offer numerous benefits, it is essential to consider security aspects to ensure the integrity and confidentiality of the system. Here are some key security considerations:
- Token Expiration: Implementing token expiration helps in reducing the risk of unauthorized access. Tokens should be valid for a limited period and automatically expire after that.
- Token Encryption: Encrypting Om Tokens ensures that the data they contain is secure and cannot be easily intercepted or tampered with.
- Token Revocation: Implementing a mechanism to revoke tokens when they are compromised or no longer needed is crucial for maintaining security.
By considering these security measures, you can ensure that your Om Tokens are used effectively and securely.
Conclusion
Om Tokens play a vital role in modern applications and services, providing secure authentication and authorization mechanisms. Understanding their functionalities, applications, and security considerations is essential for developers and system administrators



